John Durham gears up against the Alfa Bank conspiracy
And thoughts on CrowdStrike
A new filing in the Michael Sussmann case has revealed the depth of Special Counsel John Durham’s investigation. It doesn’t look good for former DNC lawyer (and former Perkins Coie partner) Sussmann or for the group that pushed the Alfa Bank/Trump hoax.
Special Counsel Durham has filed an opposition to Michael Sussmann’s motion for a bill of particulars. (To summarize, Durham argues that the 27-page speaking indictment against Sussmann “more than adequately” informs him of the charges he is facing.) Read it here.
What’s really notable about the motion is that Durham discloses the volumes of evidence to be produced to Sussmann and the number of entities and people Durham has subpoenaed.
According to this latest filing, Special Counsel Durham has produced “more than 6,000 documents, comprising approximately 81,000 pages” to Sussmann. This includes “documents received in response to grand jury subpoenas issued to fifteen separate individuals, entities, and organizations – including among others, political organizations, a university, university researchers, an investigative firm, and numerous companies.”
Let’s decipher that last sentence. Who has received a subpoena from Durham?
“Political organizations” likely refer to the DNC and the Hillary Clinton Campaign/Hillary for America.
“A university” = Georgia Tech.
“University Researchers” = the team involved in the Alfa Bank/Trump hoax.
“An investigative firm” = Fusion GPS.
“Numerous companies” = the companies involved with Rodney Joffe (named Tech Executive-1 in the Sussmann indictment).
As we have previously observed, Durham was already in possession of:
E-mail records from Joffe, the research group, and Sussmann/Perkins Coie.
Perkins Coie billing records.
Perkins Coie records (notes, etc.) relating to calls and meetings re: Alfa Bank.
Grand jury testimony.
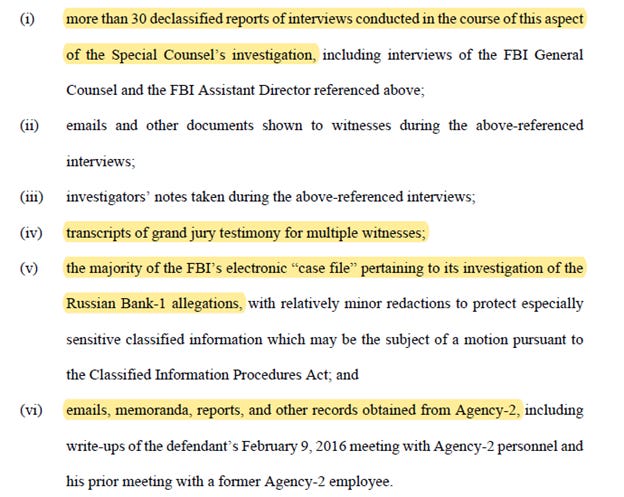
And that’s just on the Alfa Bank issue. (Durham apparently remains focused on the broader FISA issues as well as other matters.) The filing also notes that Durham is “working expeditiously to declassify large volumes of materials to provide to the defense.” This includes:
But there’s still more. Durham states after the production of these records, “the government expects to produce additional materials in subsequent productions, which will include additional interview memoranda, emails, and other records.”
Why this matters.
We anticipate that Durham is gearing-up to charge the group that created and pushed the Trump/Alfa Bank hoax. This is based on the volume of information Durham possesses on this issue, which reflects substantial expenditures of time and energy and resources to put all this together. In other words, you don’t call the grand jury on this issue - and pursue this matter this far - if the Alfa Bank researchers acted properly.
But if we are correct that the Alfa Bank researchers acted improperly – if the Trump/Alfa Bank data was manipulated – exactly how did they do it? An Ankura report from 2020 has thoughts on what went down:
This theory of manipulating the data is consistent with the communications revealed in the Sussmann indictment, where a member of the Alfa Bank “research” team explained that it would be possible to:
“fill out a sales form on two websites, faking the other company’s email address in each form,” and thereby cause them “to appear to communicate with each other in DNS.”
It also puts into context the August 22, 2016 observation from Researcher-1: “How do we plan to defend against the criticism that this is not spoofed [] traffic we are observing? There is no answer to that.”
If this is the case, then Sussmann faces more serious legal consequences than a simple false statement charge. He didn’t just take their information to the FBI and later to the CIA.
Instead, it was Sussmann who spent long hours drafting the “white paper” that summarized and explained the purported Trump/Alfa Bank links. This white paper was produced to FBI General Counsel Baker on September 19, 2016. And it was Sussmann who provided “new details concerning the [Alfa Bank] allegations” to the CIA in February 2017. Details that ultimately proved false.
This leads to the potential for potential obstruction or conspiracy charges. As we have stated, for some of this group (Joffe and some of the Georgia Tech researchers) there might be charges relating to the misuse of classified government data from DARPA.
Reconsidering CrowdStrike.
I leave you with one last thought. Aaron Mate has a great piece over at RCP discussing the history of DNC lawyers from Perkins Coie – Michael Sussmann and Marc Elias – in furthering the allegations, made through CrowdStrike, that Russians hacked the DNC.
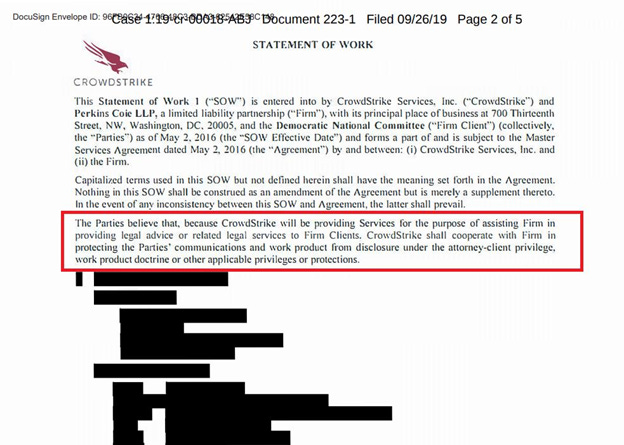
For background, Crowdstrike was retained by Perkins Coie on May 2, 2016 on behalf of their client, the DNC (and really the Hillary Clinton campaign) to assist Perkins Coie in “providing legal advice or related legal services to Firm Clients [DNC/Hillary].”
What event triggered the retention of CrowdStrike? In late April 2016, the DNC noticed suspicious behavior on its network. They contacted Sussmann at Perkins Coie, who then got the help of old friend Shawn Henry at Crowdstrike. “Within the day, the CrowdStrike team concluded that the intruders were Russian government operatives.”
In light of Michael Sussmann’s indictment and the apparent attempt by those working on behalf of the DNC to push the false Alfa Bank hoax on the FBI – consider whether the deception started earlier.
There have long been suspicions of CrowdStrike as being the entity that manipulated data showing Russians allegedly hacked the DNC/Clinton servers and extracted the e-mails.
What if Crowdstrike was a patsy, there to unknowingly reach false conclusions of a “Russian hack” based on information provided to them by Perkins Coie and the DNC?
Consider the potential that CrowdStrike was set-up to reach a predetermined conclusion by the same lawyers and political figures that gave us the Alfa Bank hoax…




The highest military honors await for you, Techno. Thank you for your service.
The problem is really the speed at which the data breech download happened. There isn't a web connection on earth that could take that much data, that quickly. It was a direct off the server to a solid state device (data fob). This is where Crowd Strike is obfuscating, and conflating information to the uninitiated data folk. They may as well be asserting they can drive from Ny to LA in 20 minutes.